On Friday afternoon, reports emerged that the NHS had been targeted by a ransomware cyber attack. Since that time, a total of at least 150 countries have been impacted, the HSE has been on high-alert and cybersecurity has become a top priority for businesses and organisations of every size.
Questions floated around late on Friday afternoon, such as who would target a health system, what is it they’re looking to gain from this and can you protect against this type of attack?
Before we get to those questions, let’s start at the very beginning.
What is a ransomware attack?
This is the name given to a particular type of cyber attack. Typically, the hacker gains access to a computer device via an email attachment or a download. This is called malware. The hacker locks all files on the computer and a threat appears on screen, declaring the user must pay a ransom to regain control of their device once more.
It’s important to note that this type of attack happens quite often and can target consumers as well as businesses.
What happened on Friday?
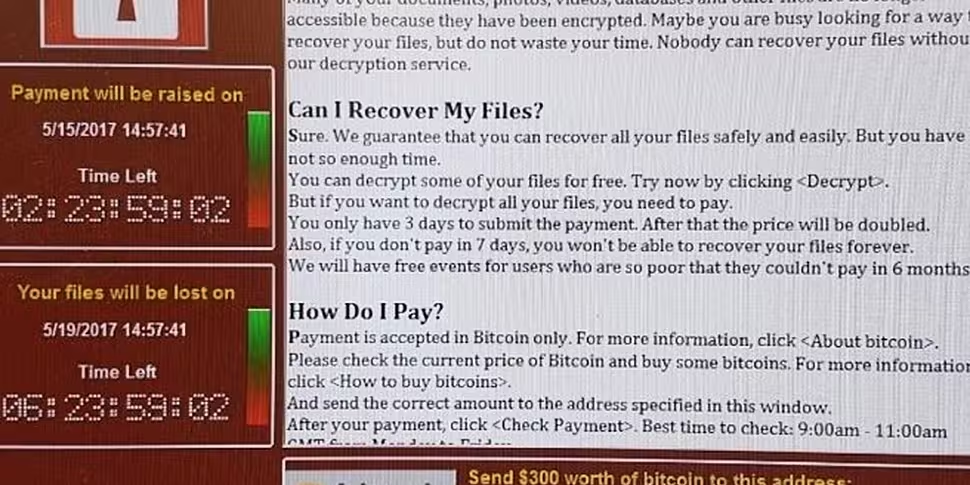
On Friday afternoon, NHS staff reported seeing computers “go down one by one”. Screenshots emerged soon after of the WannaCry programme, which demanded a Bitcoin payment of £230 to unlock the files for each computer.
Here's the malware attack which appears to have hit NHS hospitals right across England today pic.twitter.com/zIAJ6wbAG5
— Lawrence Dunhill (@LawrenceDunhill) May 12, 2017
As time went by, other countries reported infections.
Russia, Spain, Germany, France and Portugal are just some of the countries targeted. From banks and mobile networks to car manufacturers and delivery companies - a lot of industries were impacted.
What is WannaCry?
Aside from describing how most of those targeted felt on Friday, WannaCry is the name of the ransomware used in this case. It locks all files on an infected computer and demands the computer administrator pays the ransom on the screen to regain control of the device.
This tool was leaked last month as being one of a number of US National Security Agency spy tools.
This malware takes advantage of a vulnerability in Windows, which Microsoft released a security patch for in March. Any computers and networks that did not update their systems were at risk.
Microsoft says it will roll out the update to those still using older operating systems, such as Windows XP. It is thought XP is still used for the most part within the NHS.
Who is behind it?
We don't know as of yet. An international manhunt is now underway to try and track the hacker or hackers down.
Oliver Gower, of the UK's National Crime Agency, said: "Cyber criminals may believe they are anonymous but we will use all the tools at our disposal to bring them to justice."
Is it over?
In a word, no.
A 22-year old security researcher from the UK “accidentally” stopped the spread of the ransomware, but has warned that it is not over just yet.
Speaking to the BBC, the man explained how he discovered a ‘kill switch’ in the software’s code. Known only as ‘MalwareTech’, the researcher says he noticed how the malware was trying to contact a specific web address each time a new computer was infected. The web address in question had not been registered.
MalwareTech opted to buy the address for £8, meaning he could see where devices were accessing it from. He unexpectedly triggered part of the ransomware’s code that instructed it to stop spreading.
While the ransomware is no longer spreading, the devices that were targeted before MalwareTech found the ‘kill switch’ remain infected.
It is also feared that the hackers may develop a new strain of the ransomware, which could bypass the kill switch.
What about Ireland?
A small HSE-funded health care facility in Wexford has been impacted by the ransomware, however, it is important to note that it is not connected to the HSE’s network. The HSE is working to secure thousands of its devices which could take a number of days.
It is feared that many more Irish businesses may have been impacted. This will come to light on Monday, as work resumes across the country.
What can you do?
If you run Windows XP, Windows XP or Windows Server 2003, keep an eye out for the security patch from Microsoft, which is currently being rolled out. Do not download any email attachments or click on any suspect links until you have done so.
For everyone else, it’s worth downloading an anti-virus programme, if your device does not already have one. AVG is free, easy to use and does not take up too much space on your hard drive.