Two internet security firms are suggesting North Korea could be behind a global cyber attack.
Symantec and Kaspersky say they think the 'WannaCry' ransomware originated from the Lazarus group.
It has been responsible for other cyber crimes - including one targeting Sony Pictures in 2014 and an attack last year on a Bangladesh bank.
Their enquiries came as the White House said that paying ransom money to unlock files encrypted by the global cyberattack does not work.
Homeland security adviser Tom Bossett told reporters he is not aware of a case where transferring US$300 (€273) in Bitcoin - the amount demanded from victims of last week's attack - has "led to any data recovery".
The Health Service Executive (HSE) has confirmed that three hospitals, which reported cyber attack infections on Monday morning, were not from the 'WannaCry' virus.
The HSE says the 20 machines were quickly isolated from networks before it spread with the machines replaced and the systems put back online.
A spokesperson says patient care has been broadly unaffected by the disruption.
The HSE network will remain isolated for further 48 hours to maintain protection from the attack that began on Friday.
Richard Corbridge is Chief Information Officer with the HSE: "Once we were able to isolate the hospitals - take them off the network and do some investigation into each of the three hospitals - what they'd actually found was an older virus.
"The immediate reaction from any new virus coming in is remove the hospital from the network and isolate the machine... We've now since been able to ascertain that they were older viruses.
"We've been able to clean those machines and move to putting them back on to the network.
"We are treating every virus infection as if it is part of the WannaCry issue at the moment to make sure that we keep vigilance up as high as we can.
"There are around 20 machines that have been infected across three hospitals".
'Further incidences possible'
Meanwhile Communications Minister Denis Naughten has briefed a Cabinet Sub-Committee at Government Buildings.
He said: "There have been no further reported incidences of the 'Wannacry2' malware in Ireland, beyond the isolated case in a HSE funded facility in Wexford on Saturday.
"It is still possible that further incidences will arise and a sustained period of vigilance will be required, both in terms of updating and patching software and monitoring equipment."
He also told Newstalk Drive: "Nothing was targeted specifically at the HSE, this was a broad target across the globe.
"It could be that that the HSE and other State organisations had such an e-mail that was sent to them, it could have been blocked by the spam filters and various protections that are there.
"It could be in someone's inbox at this stage - and that's why we're patching up all of the equipment across the public sector, and that's really within the HSE mainly".
"It looks like that we have got away relatively lightly to compared to some other countries - but that doesn't mean that we cannot and should not continue to be very vigilant in relation to this or other threats that happen on an on-going basis".
The National Cyber Security Centre (NCSC) is monitoring the situation on an ongoing basis, and remains in close contact with international counterparts and with public and private sector entities here.
The NCSC is also cooperating with the Garda Cyber Crime Bureau and the Defence Forces, and will bring any material to the attention of the gardaí immediately.
The NCSC has issued a series of advisory notices to Government departments and agencies over the weekend.
The latest, on Monday morning, gave a detailed assessment of the malware type and of the measures that entities might take to deal with this.
Minister Naughten is bringing a memo to Cabinet Tuesday to update the Government on the situation.
The attack started hitting computers across the world on Friday, with the UK's National Health Service (NHS) among the organisations most severely affected.
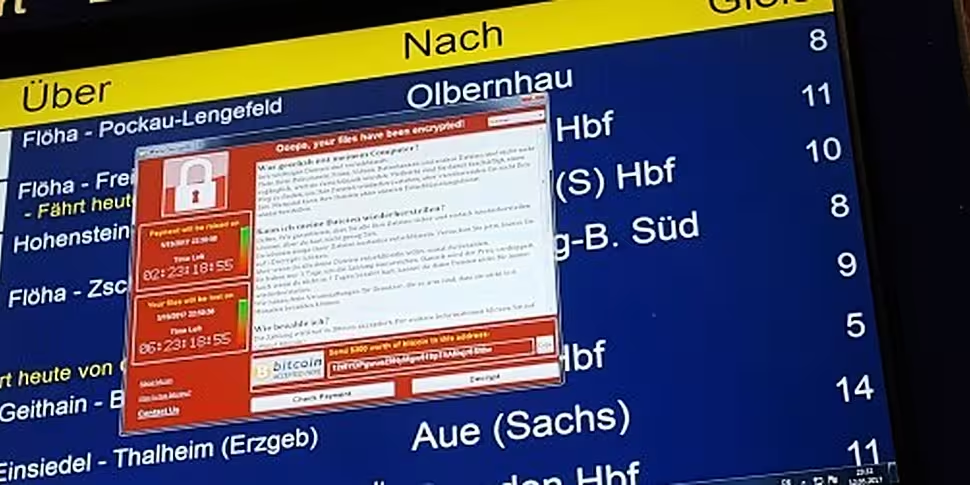
The 'WannaCry' attack - which is believed to have infected around 200,000 computers across at least 150 countries - encrypts a user's important files, with the attackers demanding a BitCoin payment to unlock the files again.
"A wake-up call"
Meanwhile, Microsoft says the attack shows the need for "more urgent collective action" over cyber security.
The software giant has blamed security exploits 'stolen' from the US National Security Agency (NSA) for the devastating cyber attack that began on Friday.
The attack is widely believed to have used a Windows exploit publicly revealed last month in leaked NSA documents.
In a blog post, Microsoft President Brad Smith argued: "The governments of the world should treat this attack as a wake-up call. They need to take a different approach and adhere in cyberspace to the same rules applied to weapons in the physical world.
"We need governments to consider the damage to civilians that comes from hoarding these vulnerabilities and the use of these exploits."
The software giant has compared the attack with "the US military having some of its Tomahawk missiles stolen".
Mr Smith repeated his company's call for a 'Digital Geneva Convention', suggesting it should include a new requirement "for governments to report vulnerabilities to vendors, rather than stockpile, sell, or exploit them".
Microsoft has released a patch for unsupported operating systems such Windows XP in a bid to halt the spread of the attack.
Additional reporting: Jack Quann